Communication involving mobile IP can be inefficient. The inefficiency can be severe or moderate. The severe case is called double crossing or 2X. The moderate case is called triangle routing or dog-leg routing.
Double Crossing
Double crossing occurs when a remote host communicates with a mobile host that has moved to the same network (or site) as the remote host.
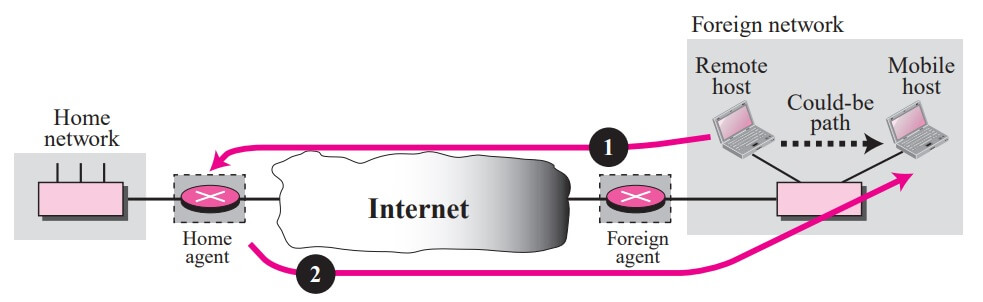
When the mobile host sends a packet to the remote host, there is no inefficiency; the communication is local. However, when the remote host sends a packet to the mobile host, the packet crosses the Internet twice.
Since a computer usually communicates with other local computers (principle of locality), the inefficiency from double crossing is significant.
Triangle Routing
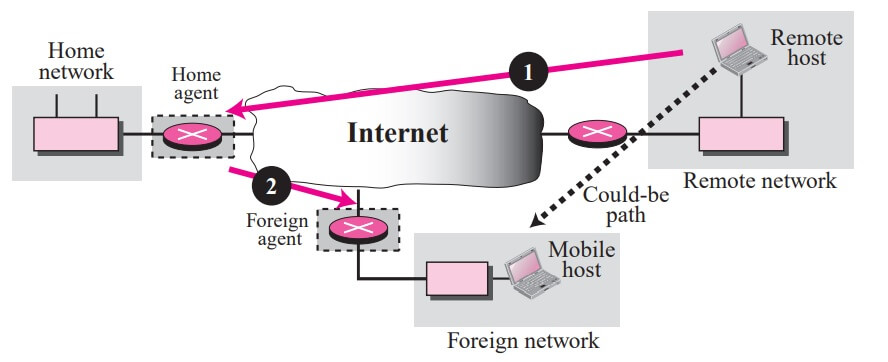
Triangle routing, the less severe case, occurs when the remote host communicates with a mobile host that is not attached to the same network (or site) as the mobile host. When the mobile host sends a packet to the remote host, there is no inefficiency. How ever, when the remote host sends a packet to the mobile host, the packet goes from the remote host to the home agent and then to the mobile host. The packet travels the two sides of a triangle, instead of just one side.
Solution
One solution to inefficiency is for the remote host to bind the care of address to the home address of a mobile host. For example, when a home agent receives the first packet for a mobile host, it forwards the packet to the foreign agent; it could also send an update binding packet to the remote host so that future packets to this host could be sent to the care of address. The remote host can keep this information in a cache.
The problem with this strategy is that the cache entry becomes outdated once the mobile host moves. In this case the home agent needs to send a warning packet to the remote host to inform it of the change.
| Read More Topics |
| Interaction between IPv4 and the datalink layer |
| TCP connection establishment in computer networks |
| The user datagram protocol |
| The transport layer in the reference model |