Power System Security
A power system security in the manual operating condition may face a contingency condition, such as a generating unit may go out of order, an important line may be tripped off, and the demand may undergo a large change from the forecasted value and so on. Although many such contingencies can occur, only those having a high probability of occurrence are to be considered and such contingencies are known as credible contingencies. A system operator would like to analyze the effect of such credible contingencies to obtain secure operation.
Thus, the analysis of credible contingencies goes to enhance the security of operation. A power system is said to be secured if there is neither any occurrence of overloading of any equipment nor transient instability due to a set of credible contingencies.
Examples of contingencies
Single credible contingency : Disconnect of generating unit, disconnection of transmission line, disconnection of transformer.
Critical single credible contingency has severe impact on power system.
Non-credible contingency : Three phase electrical faults, multiple generating unit failures, double circuit transmission line failure, abnormal conditions caused by severe weather conditions/lightning/storm/equipment malfunction.
System Response to Contingency Events
- May withstand single contingency.
- May withstand a few multiple contingencies.
- Severe violations in bus voltage, line flow and frequency.
- Loss of synchronism.
- Voltage collapse.
- Cascading outages and system blackout.
- System separation into islands.
System Security
It is defined as the degree of risk in the ability to survive imminent disturbances (contingencies) without interruption of customer service. It depends on the operating condition and the contingent probability of a disturbance. To be secure, the power system must
♦ Be stable following a contingency event and settle to operating conditions such that no physical constrains are violated (frequency, voltage magnitudes and all equipment loading within the limits).
♦ Maintained power system always in secure state.
♦ Be returned to normal operating state following a contingency.
Power System Stability : The continuance of intact operation of the power system following a disturbance.
Power System Reliability : The probability of satisfactory operation over the long run.
It is the ability to supply adequate electric a service on a nearly continuous basis, with few interruptions over an extended period.
System Black-out : Process of cascading failures continues, the entire system or large parts of it may completely collapse.
Example of black-outs:
1. July 2, 1996 – WSCC [Western North American Interconnected System]
2. August 10, 1996 – WSCC
3. November 1998 – Brazil
4. July 29, 1999 – Taiwan
5. August 14, 2003 – North East U.S and Ontario
Security Criteria (For Planning)
- Rotor angle stability.
- Voltage stability (under both steady state and contingency conditions).
- Steady state oscillatory stability i.e., dynamic stability (all real parts of Eigen values should be negative).
We must provide adequate generation capacity to meet load demand and capacity reserve, utilize resources and services provided to maintain satisfactory operating range, schedule fuel/water maintenance work, and assess situations that would affect power system security.
Operational Studies
- System load forecast for the day and week ahead on hours basis, 1 – 7 days – for scheduling adequate generation to meet security standards.
- Unit commitments – for each hour of a period of 1 – days.
- Scheduling hour by hour generations and interchange.
- Hydro-thermal scheduling including irrigation and navigation constraints.
- Optimal power flow analysis on an hourly basis.
- Power flow and stability studies to assess system security.
Security Analysis and Control
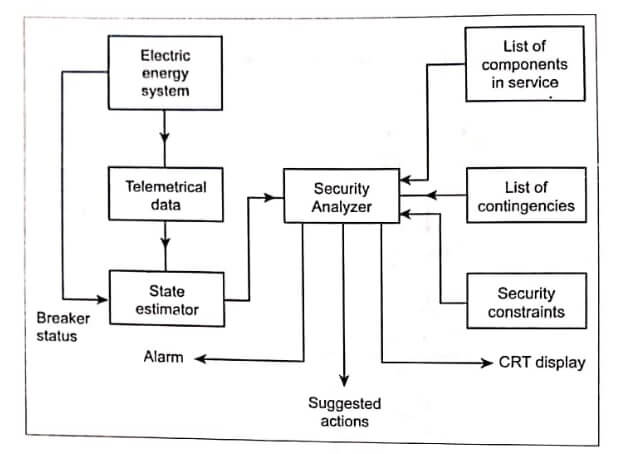
Security monitoring is the on-line identification of the actual operating conditions of a power system. It requires system-wide instrumentation to gather the system data as well as a means for the on-line determination of network topology involving an open or closed position of circuit breakers. A state estimation has been developed to get the best estimate of the complex bus voltage at any instant from the redundant set of telemetered data and breaker status. The state estimation provides the database for security analysis as shown in Fig.
The estimated values are then checked against the overload limits. If no limit is violated, the output of the estimator may be used for contingency evaluation. Hence overload limits are reached, suitable remedial measures help the operator to choose between rescheduling, line switching and load shedding.
Telemetry System (Security Monitoring System)
The functioning of a security monitoring system is shown in Fig. Effective operation of power system required that critical quantity be measured and the values of measurements be transmitted to a central location. Such systems of measurements end data transmission are called telemetry systems.
Telemetered data and information regarding breaker position received from the system are processed first by the state estimator. The output of the state estimator is then fed into the security analyzer. Other information like contingencies to be evaluated and associated constraints is also fed into the security analyzer. The security analyzer evaluates the impact of the above contingencies with the help of fast load flow techniques. Thus, the real-time data are processed in the control centres and are scanned by the security analyzer to ascertain whether the operating condition is secured.
The security monitoring functions are given below
| Function | Function performed |
| 1. Data acquisition | To process message from RTUs. check analog measurements against limits. check status values against normal value. send alarm conditions to alarm processor. |
| 2. Alarm processor | To send alarm messages. transmit messages according to priority. |
| 3. Status processor | determine status of each substation for proper connection. |
| 4. Reserve monitor | check generator MW output on all units against unit limits. |
| 5. State estimator | To determine system state variables. detect the presence of bad measured values. identify the location of bad measurements. initialize the network model for other programs. |
Power system must be designed to stabilize and to operate at acceptable voltage, frequency without loss of load. Security control executing the program by using study sequence. They are:
- Determine the system state based on current and postulated conditions.
- Create the occurrence of contingency events and determine the system state.
- For the severe contingency events, determine preventive and corrective action.
State estimators are executed depends on the demand or status change due to circuit breaker operation like opening of the line, etc. From Fig.(b) the state estimator receives information from SCADA system and the network topology and stores the state of the system (V and 8) in a central location called database. Power system application like power flow, optimal power flow, contingency analysis and short circuit analysis are executed using the state of the system were computed by state estimation.
Security Control Functions – Power System
Security Control requires the following functions.
Network Topology Processor: To determine model of the network.
State estimator: To determine best estimate of the state of the system using real time status and measurements.
Power flow: To calculate V, 8, power flows for the steady state condition.
Contingency analysis: To determine the events which are harmful to the system by determining the states.
Optimal power flow: To optimize a specified objective function by using controller action.
Security enhancement: To alleviate an existing overload in the system by using corrective control actions.
Preventive action: Before the occurrence of contingency event, preventive action has to be taken.
Bus load forecasting: To forecast the load by using real time measurements.
Transmission loss factors: To calculate the impact on transmission losses by using incremental transmission loss (ITL).
Short circuit analysis: To determine the fault current for different types of faults like LG, LL, LLG, 3Ø.
System security involves practices designed to keep the system operating when components fail. Systems security can be broken down into three major functions that are carried out in an energy control centre:
System monitoring.
Contingency analysis.
Security-constrained optimal power flow.
System monitoring : It provides the operators of the power system with pertinent upto data information on the conditions of the power system. Effective operation of the system is required that critical quantities are measured and the values of measurements are transmitted to a central location. Such systems of measurement and data transmission called telemetry systems, have evolved to schemes that can monitor voltages, currents, power systems, have evolved to schemes that can monitor voltages, currents, power flows and status of circuit breakers and switches in every substation in a power system transmission network.
Contingency analysis : The results of this type of analysis allow systems to be operated defensively. Many of the problems that occur on a power system can cause serious trouble which is often the case with cascading failures. In this analysis, certain programs are used that model possible system troubles before they arise. These programs are based on a model of the power system and are used to study outage events and alarm the operators about any potential overloads or out-of-limit voltages.
Optimal power flow : In this function, a contingency analysis is combined with an optimal power flow which seeks to make changes to the optimal dispatch of generation, as well as other adjustments, so that when a security analysis is run, no contingencies result in violations.
Factors Affecting Power System Security
As a consequence of many widespread black-outs in interconnected power systems, the priorities for operation of the modern power systems have evolved to the following :
- Operate the system in such a way that power is delivered reliably.
- Within the constraints placed on the system operation by reliability considerations, the system will be operated most economically.
- Characteristics of the Physical System (Generation, Transmission and Distribution Systems and Protection Systems)
Any piece of equipment in the system can fail either due to internal causes or due to external causes such as lightning stroke, object hitting transmission towers, or human errors in setting relays. Thus, most power systems are designed to have sufficient redundancy to withstand all major failure events.
- Business structures of owning and operating entities.
- The regulatory frame work.
Method of Enhancing Security
- Impractical to achieve complete immunity to black-out. need to strike a balance a between economy and security.
- Good design and operating practices could significantly minimize the occurrence and impact of widespread outages.
- Reliability criteria.
- Online security assessment.
- Robust stability controls.
- Real-time system monitoring and control.
- Coordinated emergency controls.
- Wide spread use of distributed generation.
Comparison between Power System Reliability and Security
Reliability is a probabilistic index defined as the long term average number of days on which daily peak load exceeds the available generating capacity. Security depends upon the reserve capacity available in a given situation and the contingency probability of disturbances. It refers to robustness of the system in comparison to disturbances.
- See More : Tap changing transformer
- See More : Series capacitor voltage
- See More : Power frequency control
- See More : Reactive power and voltage control